 Register on the forum now to remove ALL ads + popups + get access to tons of hidden content for members only!
Register on the forum now to remove ALL ads + popups + get access to tons of hidden content for members only!
|
||||||||
 Best Porn Sites Best Porn Sites
|
Live Sex | Register | FAQ | Members List | Calendar | Mark Forums Read |
| General Discussion & News Want to speak your mind about something ... do it here. |
 |
|
|
Thread Tools | Display Modes |
|
|
#51 |
|
Vintage Member
Join Date: Apr 2008
Location: In the Chill lounge.....
Posts: 1,725
Thanks: 6,794
Thanked 30,933 Times in 1,714 Posts
           |
Adobe releases out-of-band security patches – amazingly not for Flash
ColdFusion, LiveCycle and Premiere get fixed by Iain Thomson 17 Nov 2015 at 22:17 Today, Adobe released important patches for some of its other products – people still using Flash can stand down, however. Web app development kit ColdFusion has a couple of patches for versions 10 and 11 for holes that could be exploited to pull off cross-site scripting attacks. Meanwhile, BlazeDS server-side software has been updated to kill off a request forgery vulnerability. There's a single patch for Adobe's LiveCycle Data Services versions 3.0 to 4.7 to fix flaws in the PC, Mac, and Linux software. This also updates the bundled BlazeDS software to fix the above server-side flaw. Apple users using Adobe Premiere Clip version 1.1.1 will also need to apply a patch. There's a flaw in the way the mobile application handles input validation issues that needs to be fixed, but the patch is only labeled important, rather than critical. Adobe says that it hasn't seen any evidence that these flaws are being exploited in the wild, but that users should patch anyway, just to be on the safe side – certainly before hackers reverse-engineer the updates and start abusing the bugs. ® http://www.theregister.co.uk/2015/11...not_for_flash/ |
|
|

|
| The Following 8 Users Say Thank You to Rick Danger For This Useful Post: |
|
|
#52 |
|
Vintage Member
Join Date: Apr 2008
Location: In the Chill lounge.....
Posts: 1,725
Thanks: 6,794
Thanked 30,933 Times in 1,714 Posts
           |
A new password-stealing attack helps hackers to target other sites and services.
By Zack Whittaker for Zero Day December 3, 2015 -- 17:33 GMT (09:33 PST) A new "cocktail" of malware is stealing passwords before locking out Windows users from their machines. A number of badly-secured sites are redirecting visitors to sites that serve up the notorious Angler exploit kit, which helps hackers conduct drive-by attacks on visitors' computers with relative ease. This kind of attack is especially sneaky as it can be done automatically and without the user's knowledge. Once the exploit kit finds a vulnerable app, such as Flash, the kit delivers its malicious payload. According to a blog post by Heimdal Security, a widely-used data thief exploit known as Pony "systematically harvests all usable usernames and passwords from the infected system" and sends them to servers controlled by hackers. This enables hackers to acquire working logins for websites, e-commerce sites, and even corporate applications, which they could further steal data from. But then the kit drops the widely-used CryptoWall 4 ransomware, which locks user files until a financial ransom is paid. Ransomware hits thousands every week, and costs users $18 million in losses, according to estimates from the FBI. Other figures suggest the Cryptowall family alone has generated about $325 million in bitcoin ransoms. One of the best ways to mitigate the attack is to keep apps up-to-date. Backing up files on an external hard drive regularly is also recommended. Bitdefender has a preemptive "vaccine" that can prevent a machine from becoming infected with the malware. http://labs.bitdefender.com/projects...owall-vaccine/ |
|
|

|
| The Following 9 Users Say Thank You to Rick Danger For This Useful Post: |
|
|
#53 |
|
Vintage Member
Join Date: Apr 2008
Location: In the Chill lounge.....
Posts: 1,725
Thanks: 6,794
Thanked 30,933 Times in 1,714 Posts
           |
Dell, Toshiba, and Lenovo PCs at risk of bloatware security flaws
Proof-of-concept exploits have been posted online, catching the PC makers off-guard. By Zack Whittaker for Zero Day December 4, 2015 -- 23:03 GMT (15:03 PST) A trifecta of vulnerabilities has been found in software preinstalled on a number of Dell, Toshiba, and Lenovo consumer and enterprise PCs and tablets, affecting millions of users. A proof-of-concept that was posted online (which we are not linking to) could allow an attacker to run malware at the system level, regardless of what kind of user is logged in. A user can be tricked into opening a specially-crafted web page, either as a drive-by download or through an email attachment, which could allow an attacker to exploit the flaw. The security researcher, known as slipstream/RoL, confirmed to ZDNet that he did not inform Dell, Toshiba, and Lenovo of the flaws before the the proof-of-concept code was posted online. An advisory, posted by Carnegie Mellon University's public vulnerability database (CERT) on Thursday, said preinstalled Lenovo software ( often known as "bloatware" ) includes three vulnerabilities. The Lenovo Solution Center, an app designed to give the user a quick overview of the system's health, security and network status, comes pre-installed on a number of Think products, including ThinkPads, ThinkPad tablets, ThinkCenter and ThinkStation, IdeaCenter and some IdeaPads, running Windows 7 and later. A Lenovo spokesperson would not say which specific models or how many would be affected, but referred to the security advisory posted on its website, posted Thursday, which reads: "We are urgently assessing the vulnerability report and will provide an update and applicable fixes as rapidly as possible. Additional information and updates will be posted to this security advisory page as they become available." Lenovo has not said when it will fix the vulnerabilities in the software, but said in a security advisory that uninstalling the app will remove the risk posed by the flaw. As for Toshiba, a security vulnerability was found in the preinstalled Toshiba Service Station, which searches for software updates among other features. According to slipstream/RoL, the app allows a logged-in user to read parts of the registry as a system user, which has higher privileges than a standard user account. He said an attacker can't read the security account manager (SAM) or bootkeys, however. He said it's possible to "bypass any specific registry permissions set." For Dell, this is the second major security issue in as many weeks -- and both were found by the same security researcher. Slipstream/RoL said that the preinstalled Dell System Detect app, which checks a user's system for issues prior to a support call, can be crudely used to bypass a Windows security feature that escalates a user's privilege. He said that an attacker can abuse a signed application to repeatedly give a signed User Account Control prompt, until a user gives way and allows the elevation. It comes just a week after Dell was accused of preinstalling a security certificate that could allow an attacker to intercept traffic and conduct man-in-the-middle attacks. CERT explained at the time that attacker can create their own certificates signed by Dell, which would be trusted by any system that trusts that certificate. Spokespeople for Dell and Toshiba did not immediately respond to an email requesting comment. It's not clear how many PCs or tablets are affected by the flaw, but it's thought to be in the millions . Lenovo shipped 13.5 million PCs during the third-quarter this year, according to its third-quarter earnings report, published in mid-August. But it's not clear how many Lenovo PCs and tablets are affected by the vulnerable software. Based on IDC figures, Dell shipped more than 10.1 million PCs in the third-quarter. It's not clear how many Toshiba PCs were shipped worldwide, but it shipped about 810,000 PCs in the US during the third quarter. Bloatware -- also known as crapware -- remains a major issue in PC and mobile circles, particularly because it's been known to compromise system security. Lenovo, which was caught up in the "Superfish" adware scandal earlier this year, promised to stop bundling preinstalled bloatware on PCs. "Preinstalled crapware is bad, m'kay?" said the researcher. |
|
|

|
| The Following 8 Users Say Thank You to Rick Danger For This Useful Post: |
|
|
#54 |
|
Vintage Member
Join Date: Apr 2008
Location: In the Chill lounge.....
Posts: 1,725
Thanks: 6,794
Thanked 30,933 Times in 1,714 Posts
           |
White hats, FBI and cops team up for Dorkbot botnet takedown
Your four-year reign of terror is (temporarily) over By John Leyden 4 Dec 2015 at 12:50 Operations of the Dorkbot botnet have been disrupted following an operation that brought together law enforcement agencies led by the FBI, Interpol and Europol, and various infosec firms. The Dorkbot infrastructure, including command and control servers in Asia, Europe, and North America, has been knocked sideways and domains seized, with the latter affecting the ability of crooks to control compromised computers. Infected Windows PCs will still need to be cleaned up, however. Dorkbot has been doing the rounds for more than four years, essentially since April 2011. Security firms, including ESET, shared technical analysis of Dorkbot. The information included the domains and internet addresses of the botnet’s command and control servers, vital intelligence for the subsequent takedown operation. Microsoft and CERT.PL also assisted in the disruption effort. Dorkbot is a well-established botnet distributed via various channels, such as social networks, spam, removable media and exploit kits. The malware is a password-stealer targeting popular web services, such as Facebook and Twitter. Dorkbot typically installs secondary malware on compromised machines. Favourite flavours include Kasidet (AKA Neutrino bot), malware used to conduct DDoS attacks and Lethic, a well-known spambot. Unwitting conduits for spreading the infection included celebrity cook Jamie Oliver's website back in February. |
|
|

|
| The Following 7 Users Say Thank You to Rick Danger For This Useful Post: |
|
|
#55 |
|
Vintage Member
Join Date: Apr 2008
Location: In the Chill lounge.....
Posts: 1,725
Thanks: 6,794
Thanked 30,933 Times in 1,714 Posts
           |
PCMag.com
August 25, 2015 REVIEW Bitdefender Box  Editor's Rating: Excellent MSRP: $199.00 Lowest Price: $199.00 Amazon: $199.00 +Free Shipping Pros Elegant design. Protects an unlimited number of local devices on your network. Advanced on-the-go device management. Private Line protects devices even when they're not in your home. Smart setup can augment existing wireless network. Cons Poor performance as a stand-alone router. Difficult to differentiate devices in network browser. No Web interface. Bottom Line A paradigm shift for the consumer security industry, Bitdefender Box is a piece of hardware that protects every computer, phone, tablet, and smart device on your network. It does a surprisingly good job, considering it's the first device of its kind. By Max Eddy, with Fahmida Y. Rashid and Neil J. Rubenking For decades, consumers have been using antivirus software to protect against all the nasty things on the Internet that could hurt their Mac or Windows computers. This has even extended to mobile phones, and now even Android antivirus is a growing software category. But the Bitdefender Box destroys this model. Instead of a software solution, the Bitdefender Box is a piece of hardware that connects to your network and protects all of your devices; from your phone, to your fridge, to your computer, to your PlayStation, and more. It's a completely new paradigm in consumer security. The Bitdefender Box costs $199 and comes with one free year of service. After that, protection costs $99 a year for an unlimited number of devices. The Box isn't cheap, but it actually works out to be quite a bargain: Bitdefender Total Security, for example, covers only three computers for $89. And that doesn't include protection for mobile devices, or Internet of Things devices, either. Once you really start thinking about how many devices connect to your Wi-Fi network, the Box quickly starts to look like a sweet deal. The Hardware Extremely small and light, the Bitdefender box measures 1.1 by 3.5 by 3.5 inches (HWD) and weighs a mere 3.25 ounces.It looks like a thicker, white Apple TV$174.99 at Bonanza with a downward facing blue LED that gives the front of the Box an otherworldly glow. The comparison to Apple is a compliment to the Box's design, but it was apparently a hard-won success. Bitdefender told us that the process of selecting the materials and finish for the Box was an arduous one, but the effort clearly paid off.  Bitdefender Box The Box is powered by a single-core 400MHz MIPS microprocessor, 16MB Flash memory, and 64MB DDR2 RAM. There are two 10/100 Ethernet ports, a power port, and a reset button in the back. The wireless chipset supports 802.11b/g/n, but we aren't talking top of the line hardware specs here. It's just enough for what it has to do. The LED on the front glows teal when operating normally, flashing teal when being configured, red if there is a problem, and white when it's performing an update. Setting Up All the Ways To get started, simply plug the Box into your router via the included Ethernet cable, and then plug the included USB cable and converter into any standard power outlet. The Box requires very little power—we saw one connected to a portable rechargeable battery—so you could conceivably connect it directly to a powered USB port on your router or computer. Once the Box is connected, you download either its associated Android or iOS app (sorry Windows Phone; you're still protected but you can't configure the Box) and create an account. If you already have a MyBitdefender account from one of the company's other products, you can just sign in with that. We installed the app on both a Nexus 5$224.95 at Amazonphone and a Nexus 7$177.17 at Amazon tablet and had no trouble accessing the Box settings that way. Bitdefender Box has a long list of supported routers. If you have one of those routers, the app will communicate through your Wi-Fi network and set up the Box automatically. Our lab testing environment is powered by a Netgear Nighthawk X6 AC3200 Tri-Band WiFi$299.99 at Dell router and has a variety of devices connected. This router wasn't supported by the Box, but it was included in Bitdefender's manual setup documentation. The entire process of manually configuring the router took about 15 minutes from start to finish. It wasn't particularly challenging, but it did test our patience. Once set up, we were pleasantly surprised that the device performance impact on a network secured by the Box was so slight. The difference between having the Box on the network and no Box was less than 5 percent, with speeds dropping to 176Mbps, down from 184Mbps at a distance of 15 feet. Since this is a consumer product, we wanted to see how the experience would be on a typical home's Internet connection and so set up the Box on a residential DSL line at PCMag's secret Brooklyn laboratory. This connection used PPPoE, which Box supposedly supported though we triggered an error every time we entered the username and password. This was one instance where the lack of detail on the app was really frustrating. Some login screens allow you to view your password in plaintext to check for typos. There's no way to do that with the Box app. We cut-pasted the password from LastPass$12.00 at LastPass, keyed it in carefully, and each time we are sure we are giving the correct credentials, all to no avail. In the end, we tried a cable modem with DHCP. This time, the setup experience was seamless. It's what BitDefender promised, and it delivered. BitDefender said the company had originally created a Web interface for configuring Box, but decided it was too complicated for users. There is also a good security reason, since putting a Web interface means you are essentially running a (albeit, small) Web server on the device. Dropping the Web interface is a smart security move, but it may be a smidgen ahead of its time. Protecting Everything When Bitdefender says that the Box protects every device, they mean every device: Your printer, your desktop computer, your laptop, your sundry smartphones, your various tablets, your gaming consoles, your Nest smart thermostat, your smart fridge, your Philips Hue lights, and so on. Many of these devices are completely closed to the user and can't have antivirus protection installed. The Box protects every device connected to your Wi-Fi network using a super-fast, cloud-based malware detection engine. This includes anyone who connects to the network, for however long they stay connected. If something untoward happens regarding any of the connected devices, Bitdefender will block the threat and send you a message through the app. 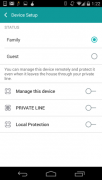 This model shifts protection to your Internet connection, stopping bad stuff before it ever reaches your computer. But you can also use the Box app to install a local agent to provide on-device protection for associated Windows, Mac, and Android devices. Think of it as antivirus lite, to keep an eye out against infected USB drives or other offline attacks. We rely on information from independent labs for many antivirus products, but none of the labs have yet looked at the Bitdefender Box. They have, however, looked at Bitdefender's other software offerings. AV-Test found that Bitdefender Mobile Security detected 100 percent of Android malware, Bitdefender Internet Security detected 100 percent of Windows malware, and Bitdefender Antivirus for Mac detected 100 percent of OS X malware. Similarly, AV-Comparatives found that Bitdefender's software detected 99 percent of Mac malware, 99.6 percent of Android malware, and 99.8 percent of Windows malware. Once the agent is installed on your desktop computer, you can use the Box app to trigger OS updates, install patches, and even let you perform basic cleanup actions on the protected computer. We weren't able to test these functions as our Apple iMac was already patched and up-to-date. In our testing, we found that the Box blocked 16 percent of malicious URLs provided by MRG Effitas. When running this test on antivirus software suites, we've found an industry average of over 30 percent. These somewhat middling scores are a little disappointing considering that the Box is designed to put Internet security first. However, Box's performance is spot-on with its desktop software equivalent from Bitdefender, so at least we know it's probably the same software inside the Box. We also found that Box successfully blocked infected links in emails, tricky URLs that redirect you from safe sites to suspicious ones, and successfully flagged eight out of 10 phishing URLs from phishtank.com. Since the purpose of Box is to prevent bad things from coming in from the Web, we didn't subject the Box to our usual battery of live malware tests. However, we did confirm that the Box's antivirus features were operating with the EICAR testing applications. These are benign pieces of software designed to be detected by antivirus engines to ensure malware protection is functioning properly. Device Management Once activated, the Box app will populate with the devices on your network. For the average home with just a handful of devices, this will be a snap. For the super-geeky home with tons of devices, it's a little more challenging. On the network tab of the app (the center one) you'll see your Family devices and your Guest devices. Anything that connects to your network will appear as a Guest in the app, identified by cryptic descriptors like "A smart TV" or "BLACKBERRY-B5D9." You can rename these devices, add images, and even associate them with contacts from your address book, but because Bitdefender doesn't show you the MAC or IP address of the devices, figuring out which is which is tricky. Despite testing across three different testing environments, we never quite got the hang of how to get Box to "see" devices as active. Box would clearly display a Blackberry device in its list, for example, and we were able to move it to the "Family" tab to monitor its activity. But the activity indicator was always at "idle." Box was not seeing its activity while it was in use—which was strange, as we weren't browsing HTTPS or other encrypted sites. The Nexus 5 phone and the Windows 7 laptop, however, came up as active when we were using them. We believe this is a problem with specific devices not receiving new DHCP settings after the Box was connected to the network. Not a Solo Act Bitdefender told us that although the Box can function as a stand-alone router, its real strength is augmenting an existing Wi-Fi network. That way, you keep your router, and you won't have to update the password information for all of your associated devices. When we tested the Box as a standalone router, we quickly discovered it also just wasn't powerful enough to cut the mustard.  Bitdefender BoxBox supports 802.11b/g/n. That means that in standalone mode, Wi-Fi performance won't be nearly as good than if you were using a 802.11ac router. In our testing, both Netgear routers we used supported 802.11ac as both Netgear routers we used were. In the standalone test using the jperf utility, Box averaged 93Mbps at about 1 foot, 70Mbps at 10 feet, and down to 64Mbps by the time we got to 15 feet. The Box couldn't maintain the signal long enough to even try testing at 20 feet. In practical terms, this means moving further from the Box severely degrades your network performance. Ten feet with direct-line-of-sight seems to be ideal, so using the Box as a stand-alone router really makes no sense. We measured Internet performance using SpeedTest.net. With the regular Netgear router on its own, we saw Internet download speeds of 2.89Mbps and uploads of 0.41Mbps. Switching to the Box dipped that figure only slightly, to 2.86Mbps download and 0.38Mbps uploads. Most people won't notice a difference, especially if they are on faster broadband connections. When we paired Box with the Netgear Nighthawk (R7000) router, in the recommended configuration, we saw Internet download speeds of 2.87Mbps and upload speeds of 0.40Mbps. Clearly, the Box doesn't impact Web browsing. Beyond Your Home Box's Private Line feature extends malware protection to Mac, Windows, and iOS devices that are currently out of range of your protected Wi-Fi network. Once enabled, your traffic is routed through and protected by the Box no matter where the device is or how it's connected to the Internet (be it Wi-Fi or cellular). It's your very own VPN service.Bitdefender Box The feature worked as expected in testing, as we continued to see alerts about potential malicious activity on our tablet even when we were outside and connected to a cellular network. This can be quite handy if you happen to open up a malicious email while out and about, as Box will be able to step in and block the URL. We were worried that Private Line would slow down Web performance since it routes device's connection back to where the Box is located, and then out to the Internet. While there was a performance hit, it wasn't as bad as expected, with Internet download speeds of 2.5Mbps and upload speeds of 0.35Mbps. However, we did notice screen fragments when using desktop sharing tools such as WebEx and VNC. Out of the Box We used the Box for months and on many networks, learning its ins and outs. Throughout our testing, we had a hard time seeing what devices were on our network, and trying to manage them in real time. The app, while simple, is sometimes too simple and didn't always give us the insight or tools we needed. We also had trouble resetting the Box for new networks—something the average user probably not have to do often. But we also found the Box to be remarkably powerful. Just by plugging in the Box to our network, we had the protection of an entire antivirus suite, at a lower cost and without the effort of installing software on every device. Its Private Line feature offers the protection of a VPN, but the assurance of your own trusted network. And it can't be understated that the Box solves the problem of having dozens of Internet connected devices that can't be secured through traditional means. Bitdefender has entered new territory with the Box, and it's a great first start. We're confident that Bitdefender will improve setup and management. It's the first device of its kind, and we hope it won't be the last. Max Eddy is a Junior Software Analyst investigating the latest and greatest apps for Android. Paranoid by nature, he's also keeping an eye on emerging threats and countermeasures at SecurityWatch with Neil Rubenking and Fahmida Rashid. Prior to PCMag, Max wrote for the International Digital Times, The International Science Times, and Geekosystem.com. You can follow him on Twitter at @wmaxeddy, or via email at max_eddy@pcmag.com. |
|
|

|
| The Following 8 Users Say Thank You to Rick Danger For This Useful Post: |
|
|
#56 |
|
Vintage Member
Join Date: Apr 2008
Location: In the Chill lounge.....
Posts: 1,725
Thanks: 6,794
Thanked 30,933 Times in 1,714 Posts
           |
All Windows users should patch these critical security flaws
The company issued 12 bulletins fixing dozens of vulnerabilities in Windows, Windows Server, Internet Explorer, and Office, and other products. By Zack Whittaker for Zero Day December 8, 2015 -- 18:39 GMT (10:39 PST) Another month, another batch of major Windows security flaws. Microsoft said Tuesday as part of its its monthly security bulletin that all Windows users should patch their systems to prevent attackers from exploiting at least two critical flaws. MS15-128 fixes a series of graphics memory corruption flaws, which can allow an attacker to install programs, view and delete data, and create new accounts with full user rights. The flaw, which affects Windows Vista and later , also affects Skype for Business 2016, Microsoft Lync 2010 and Lync 2013, as well as Office 2007 and Office 2010. Another major flaw, MS15-124, affects all supported versions of Internet Explorer, which can allow an attacker to to gain the same user rights as the current user. Those running as an administrator would be most affected by the flaw. Some of the vulnerabilities in this bulletin also affect Microsoft Edge, the company's new browser that lands on Windows 10. An attacker would have to "take advantage of compromised websites," said the advisory. "These websites could contain specially crafted content that could exploit the vulnerabilities." An attacker could also convince a user to open a web page from an email. Both of these flaws were privately reported and are not thought to have been exploited in the wild. Here's the rundown for the other critical flaws: MS15-126 addresses critical flaws in JScript and VBScript, which could allow an attacker to gain the same rights as the current user. The flaws affect Windows Vista and Windows Server 2008 (and Server Core installations).Microsoft also released four other patches -- MS15-132, MS15-133, MS15-134, and MS15-135 -- for "important" issues relating to Windows. December's patches will be available through the usual update channels. |
|
|

|
| The Following 7 Users Say Thank You to Rick Danger For This Useful Post: |
|
|
#57 |
|
Vintage Member
Join Date: Apr 2008
Location: In the Chill lounge.....
Posts: 1,725
Thanks: 6,794
Thanked 30,933 Times in 1,714 Posts
           |
Apple Releases Multiple Security Updates
Original release date: December 08, 2015 | Last revised: December 09, 2015 Apple has released security updates for iOS, tvOS, OS X, watchOS, Safari, and Xcode to address multiple vulnerabilities, one of which could allow a remote attacker to take control of an affected system. Updates available include: iOS 9.2 for iPhone 4s and later, iPod touch (5th generation) and later, iPad 2 and laterUS-CERT encourages users and administrators to review Apple security updates for iOS 9.2 (link is external), tvOS 9.1 (link is external), OS X El Capitan 10.11.2 and Security Update 2015-008 (link is external), watchOS 2.1 (link is external), Safari 9.0.2 (link is external), Xcode 7.2 (link is external) and apply the necessary updates. |
|
|

|
| The Following 4 Users Say Thank You to Rick Danger For This Useful Post: |
|
|
#58 |
|
Vintage Member
Join Date: Apr 2008
Location: In the Chill lounge.....
Posts: 1,725
Thanks: 6,794
Thanked 30,933 Times in 1,714 Posts
           |
Adobe's final patch update this year: 78 bugs squashed
Adobe has issued its last 2015 security update, fixing a total of 78 security vulnerabilities. By Charlie Osborne for Zero Day December 9, 2015 -- 13:41 GMT (05:41 PST) Adobe has issued the company's last security update which patches a total of 78 CVE vulnerabilities in Flash Player, seven of which are deemed high-risk. The software giant has recently renamed its Flash Professional product to Animate, no doubt to distance the product from the bug-riddled and somewhat untrustworthy Flash Player, but a simple renaming of the product family, unfortunately, does not erase security flaws. In the last patch round scheduled for this year, Adobe's latest set of security updates are specially targeted at Adobe Flash Player and address issues which "could potentially allow an attacker to take control of the affected system," according to the software developer. Adobe Flash Player Desktop Runtime versions 19.0.0.245 and earlier, Adobe Flash Player Extended Support Release 18.0.0.261 and earlier, Adobe Flash Player for Google Chrome versions 19.0.0.245 and earlier on Windows, Mac, Linux and ChromeOS systems are all affected. In addition, Adobe Flash Player for Microsoft Edge and Internet Explorer 11 19.0.0.245 and earlier on Windows 10, Adobe Flash Player for Internet Explorer 10 and 11 versions 19.0.0.245 and earlier on Windows 8.0 and 8.1 and Adobe Flash Player for Linux versions 11.2.202.548 and earlier are all subjects of this round of patch updates. AIR Desktop Runtime versions 19.0.0.241 and earlier, AIR SDK 19.0.0.241 and earlier, AIR SDK & Compiler 19.0.0.24 and AIR for Android versions 19.0.0.241 and earlier are impacted. The security flaws fixed in this update include security bypass vulnerabilities, heap buffer overflow bugs, a dozen memory corruption vulnerabilities, stack overflow weaknesses and dozens of use-after-free vulnerabilities that could lead to remote code execution. Researchers from Google Project Zero, HP's Zero Day Initiative, the Chromium Vulnerability Rewards Program and Qihoo 360 contributed to the update, among others. In October, Adobe patched a total of 23 vulnerabilities in Flash Player which were deemed critical, as well as patching bugs in software including AIR Desktop Runtime, AIR SDK & compiler and AIR for Android. |
|
|

|
| The Following 7 Users Say Thank You to Rick Danger For This Useful Post: |
|
|
#59 |
|
Vintage Member
Join Date: Apr 2008
Location: In the Chill lounge.....
Posts: 1,725
Thanks: 6,794
Thanked 30,933 Times in 1,714 Posts
           |
Google Releases Security Update for Chrome
Original release date: December 08, 2015 Google has released Chrome version 47.0.2526.80 to address multiple vulnerabilities for Windows, Mac, and Linux. Exploitation of one of these vulnerabilities may allow a remote attacker to take control of an affected system. Users and administrators are encouraged to review the Chrome Releases (link is external) page and apply the necessary update. http://googlechromereleases.********...able%20updates |
|
|

|
| The Following 5 Users Say Thank You to Rick Danger For This Useful Post: |
|
|
#60 |
|
Vintage Member
Join Date: Apr 2008
Location: In the Chill lounge.....
Posts: 1,725
Thanks: 6,794
Thanked 30,933 Times in 1,714 Posts
           |
Google's December 2015 Security Update is live, here's what you need to know
By Russell Holly Monday Dec 7, 2015 at 2:08 pm EST In keeping with their promise to make Android more secure on a monthly basis, Google's December 2015 Security Bulletin has been posted, detailing the next update and what was addressed this time around. According to Google, partners were notified and provided updates for the December list on November 2nd. AOSP will be updated with patches over the next 48 hours, and firmware images for this update are available now on the Google Developers site. This update is marked December 1, 2015 on phones that mark security updates in settings, for example the BlackBerry Priv which has already received this update. 16 CVEs — that's Common Vulnerability and Exposures ID for those who don't speak security codenames — are addressed in this update, and according to Google there are no active reports of any active exploits through these vulnerabilities. These vulnerabilities were discovered by 11 different individuals, four of which are part of Google's Chrome Security Team or Project Zero. Details for these vulnerabilities can be found in the security bulletin, but largely the issues addressed mediaserver vulnerabilities, file manipulation leading to remote code execution, and the privilege elevation in libstagefright that caused so much concern recently. Google's continued push for monthly updates isn't surprising given how new this program is, and seeing BlackBerry push ahead with updates before Google is impressive, but the biggest win for this initiative so far has been Samsung' recent decision to include the security patch level on non-Marshmallow phones, signifying the company is interested in cooperating and keeping users safe. See you next month for more! http://www.androidcentral.com/google...-you-need-know |
|
|

|
| The Following 6 Users Say Thank You to Rick Danger For This Useful Post: |
 |
| Thread Tools | |
| Display Modes | |
|
|